USB Sticks – Most Favorite Of Virus Writers
USB thumb drives are convenient and popular but they’re the biggest source of spreading viruses as well. Mmalicious USB sticks are leveraged where an attacker needs physical access to a computer. A malicious USB device can install a wide range of malware such as backdoors, trojans, and information stealers.
They can also install browser hijackers that will redirect a victim to the hacker’s website of choice, which could host more malware, or inject adware, spyware or greyware on target computers.
Examples of Malware Distributed via USB Sticks
STUXNET – the worm launched attacks on the networks of Iranian nuclear facilities and destroyed more than a thousand centrifuges.
DUQU – collection of computer malware steals digital certificates and cryptography private keys from attacked computers. It also deletes data from the infected computers.
FLAME – also known as Flamer and Skywiper, is modular computer malware, being used for targeted cyber-espionage in Middle Eastern countries.
AGENT.BTZ – a variant of the SillyFDC worm that infects USB flash drives with spyware and it was used in a massive cyber-attack on the US military.
Data Resides on USB Sticks after Deletion
We use USB sticks, for convenience, to carry files (even secret data) for transfer, printing or other purposes. Although, we delete the data but “actually” the data still stays on the drive and most of the times can be recovered using publicly available data-recovery tools.
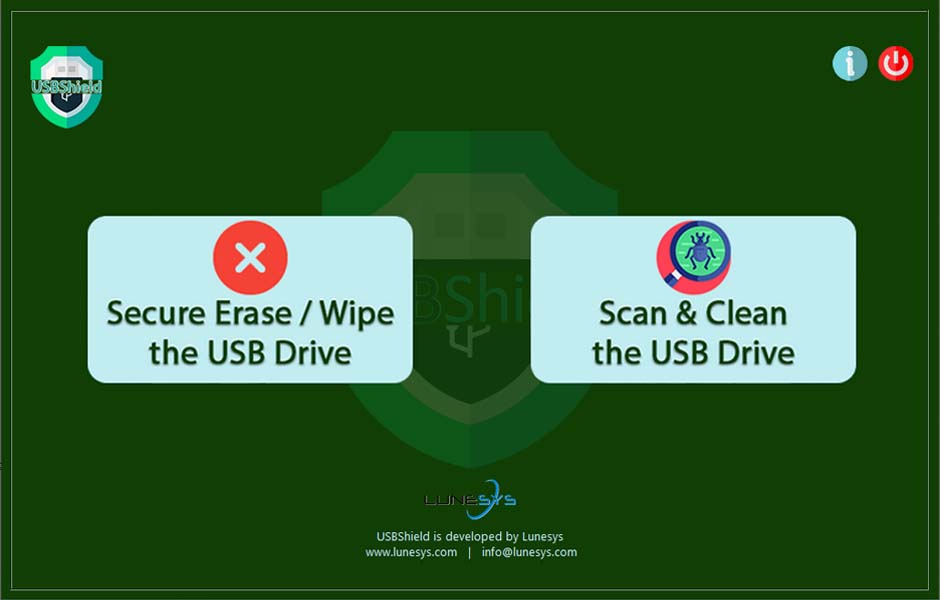
USB-Shield
A Dedicated Box for USB Sticks Security – to Secure-Erase against Data-Theft and Scan & Clean against Malware
USB-Shield is a dedicated box that gives users two options:
- Securely (permanently) erase the USB stick so that the data is no-more recoverable
- Scan and clean the USB stick against viruses/ worms/ malware/ trojans/ backdoors
Lunesys’ Other Services
Penetration Testing
Determine security weaknesses!Blackbox, Whitebox or Greybox
Test your organization’s security policy compliance, employees’ security awareness and the ability to identify and respond to security incidents.
ISO/IEC 27001
Demonstrates to your clients that you have secure data and robust systems.Information Security Management System
ISO/IEC 27001 helps you implement a robust approach to managing information security (infosec) and building resilience.
Digital Forensics
The incident was not the end of the world. We can backtrack!Uncovering and Interpreting Electronic Data
We collect, analyze and report on digital data in legally admissible ways.
Cybersecurity Benchmarking
Lunesys will benchmark your organization’s cybersecurity postureNIST Cybersecurity Framework Benchmark
Identify current and targeted future state of your organization’s security program utilizing the Top 20 Critical Security Controls and NIST Cybersecurity Framework Categories.
Why Choose Lunesys
-
-
- We are not a jack-of-all-trades involved in every sort of business and training;
- We are focused on information security management purely, which rally us round understanding and facilitating the clients’ specific need;
- We have an extensive range of highly qualified trainers, a comprehensive range of professional public training courses, enabling the potential participants to hit upon and sign up for exactly the training they need, in their most suitable time span;
- We don’t only provide trainings but also offer the implementation of the theories, which gives us an edge to assist the participants later in their practical epochs;
- The most reasonable price is another advantage we offer;
- Our previous clients’ great satisfaction and highly-rating testimonials are our honor.
-